Table of Contents
- Executive Summary
- Network Validation Sector Brief
- Decision Criteria Analysis
- Analyst’s Outlook
- Methodology
- About Ivan McPhee
- About GigaOm
- Copyright
1. Executive Summary
As networks become increasingly complex with proliferating cloud services, edge computing, and IoT devices, the risk and impact of misconfigurations and outages escalates. A single error can expose security vulnerabilities, negate compliance, or cause widespread downtime. Network validation solutions are essential for maintaining a reliable and secure network despite constant changes, ensuring a network infrastructure operates as intended and meets the requirements and expectations of its users and stakeholders.
To accomplish this, organizations require a modern, disciplined approach to network change management, ensuring compliance across all network devices and services. Figure 1 depicts the network change management process required to maximize the uptime of business-critical applications and processes while enhancing the user experience. While scope determination, risk analysis, and peer review are manual processes, validating network changes both before and after implementation needs to be automated, accelerating the process and reducing risk by injecting consistency and discipline.
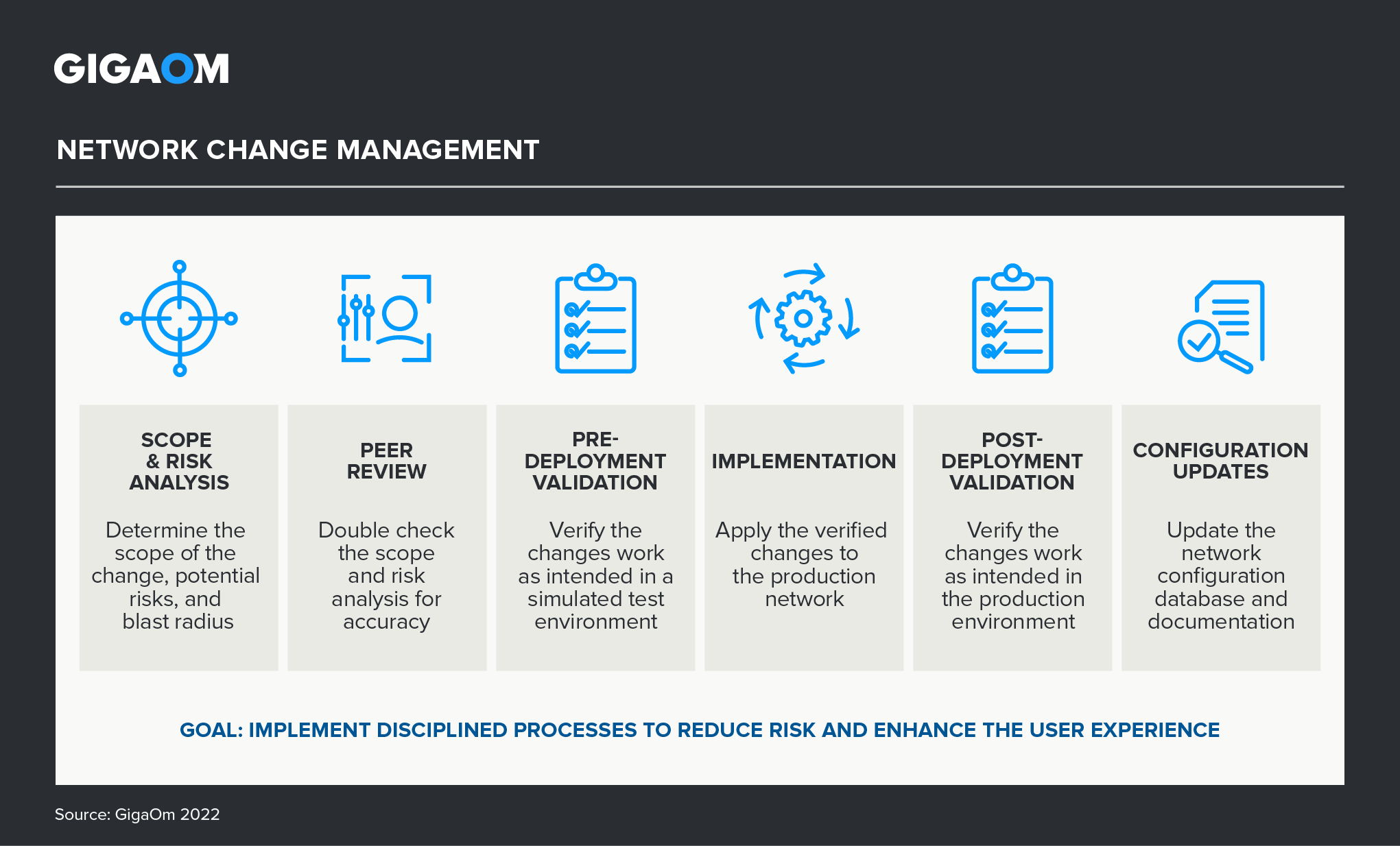
Figure 1. The Network Change Management Process
Network validation solutions leverage techniques like configuration analysis, data plane testing, and active monitoring to comprehensively assess network health, performance, and compliance:
- Configuration analysis: This process scans network device configurations for errors, inconsistencies, and deviations from defined standards and policies.
- Data plane testing: Generates synthetic traffic to verify end-to-end network paths, access control lists (ACLs), quality of service (QoS), and other data plane functions.
- Active monitoring: Continuously polls network devices and services to validate availability, reachability, and performance against baselines.
The importance of network validation cannot be overstated, as it helps prevent network failures, security breaches, and performance issues. By proactively identifying and addressing potential problems, network validation minimizes downtime and enhances the overall efficiency of network operations. Moreover, this proactive approach is more cost-effective in the long run compared to reactive measures, which often involve addressing issues after they have already impacted the network. Furthermore, network validation supports compliance with regulatory standards and business requirements, ensuring network changes align with the intended design and operational goals.
Business Imperative
In today’s connected world, the network is the lifeblood of the business. Any disruptions or security breaches can have severe financial and reputational consequences. A network validation solution is a critical risk management tool that assures CxOs the network is operating reliably, securely, and in compliance with the business intent. Continuously validating network state and behavior, network validation solutions enable organizations to confidently accelerate IT initiatives, proactively mitigate network issues before they impact users, and ensure the network remains a strategic business enabler.
Sector Adoption Score
To help executives and decision-makers assess the potential impact and value of deploying a network validation solution, this GigaOm Key Criteria report provides a structured assessment of the sector across five factors: benefit, maturity, urgency, impact, and effort. By scoring each factor based on how strongly it compels or deters adopting a network validation solution, we provide an overall Sector Adoption Score (Figure 2) of 4.6 out of 5, with 5 indicating the strongest possible recommendation. This means that a network validation solution is a credible candidate for deployment and worthy of thoughtful consideration.
The following Sector Brief section explains the factors contributing to the Sector Adoption Score for network validation in more detail.
Key Criteria for Network Validation Solutions
Sector Adoption Score
Figure 2. Sector Adoption Score for Network Validation
This is the third year that GigaOm has reported on the network validation space in the context of our Key Criteria and Radar reports. This report builds on our previous analysis and considers how the market has evolved over the last year.
This GigaOm Key Criteria report highlights the capabilities (table stakes, key features, and emerging features) and nonfunctional requirements (business criteria) for selecting an effective network validation solution. The companion GigaOm Radar report identifies vendors and products that excel in those decision criteria. Together, these reports provide an overview of the market, identify leading network validation offerings, and help decision-makers evaluate these solutions to make a more informed investment decision.
GIGAOM KEY CRITERIA AND RADAR REPORTS
The GigaOm Key Criteria report provides a detailed decision framework for IT and executive leadership assessing enterprise technologies. Each report defines relevant functional and nonfunctional aspects of solutions in a sector. The Key Criteria report informs the GigaOm Radar report, which provides a forward-looking assessment of vendor solutions in the sector.